Be Curious – Tinker, Learn and Grow
Jonathan Studebaker, Senior Security Consultant at InGuardians, Inc.
Editor’s Note: Part 1 of this three-part series discussed the pros and cons of some common learning approaches, information resources for infosec topics that may interest you, ways to get involved in the infosec community, and setting realistic goals, budgets, and expectations for yourself to maintain work/life balance.
Part 2 discusses some specific training resources and projects like building a home lab, tinkering with Raspberry Pi, and ways to explore mobile, cloud, wireless, and physical security.
Part 3 will provide a simplified direct reference list with links and resources broken down by topic, with the intention to provide periodic updates as resource relevance and availability change over time.
The purpose of this blog post is to give you some options for exploring and tinkering with different topics within the information security space. While neither comprehensive nor definitive, these tools and projects are meant as a jumping-off place to get you started. I also want to stress that the projects and resources referenced are entirely optional. The goal should be to explore your curiosity and tinker so that you get the most out of it in a safe and secure way.
Play Online Interactive Challenges and Capture the Flags (CTFs)
Capture the Flags are challenges that teach security topics and techniques in a gamified manner with the goal of obtaining proof of successful exploitation in the form of a flag. If you think you may prefer a hands-on experience with live online CTF labs and challenges, several free and paid options are available. The difficulty and type of available challenges usually vary over time, but these types of activities can keep your skills sharp, introduce you to new concepts, and provide a way to interact with other individuals and teams in the security community.
- Hackthebox (Challenges for network, web, mobile, RE, binary exploitation, etc.)
- Portswigger Web Security Academy (Web apps and APIs)
- SANS Holiday Hack challenges
This is not a comprehensive list and there are many other online resources available that have covered this topic in far greater depth.
Writeups and guides for past challenges are also available for many CTF challenges and platforms. These can provide an interesting read if you’re not quite ready to dive into live challenges yet.
Build a Home Lab
A primary consideration of this lab should include network monitoring, isolation, and control of what gets in and out. This will give you the freedom to tinker and explore in a safe environment that will not impact other systems and devices on your network. I highly recommend checking out How to Build a Home Lab for details to create one possible solution.
If you have old hardware collecting dust in your closet or basement, dig it out and see what can be repurposed for your lab. Old laptops, desktops, servers, Raspberry Pis, and a variety of networking equipment can be used for this purpose. If you don’t have dedicated networking devices that will suit this need, check the above video link for some great cost-effective solutions and how to attach and configure them for use in the environment.
If you don’t have an old computer for your Virtual Machine (VM) server, another excellent option for a home lab setup is a mini-PC like an Intel NUC. The small form factor of these devices makes them an appealing option since they can fit just about anywhere in a typical home or office. Despite the small form factor, these devices can pack quite a punch, with modern processors and RAM options commonly available up to 64 GB. When paired with VMWare ESXi, Proxmox VE, or your hypervisor of choice, they are more than capable VM hosts. However, depending on the model and the hardware configuration, the devices can come in anywhere from around $500 to more than $1000.
If a new mini-PC is out of your price range, consider checking out sources like eBay and Craigslist for used network and computer equipment. For example, at the time of this writing a used ESXi server with dual Xeon E36440 processors, 96GB of RAM, and a 2.1TB RAID 5 array was available within driving distance for $150. These kinds of deals don’t last very long, but with a little patience and persistence, it’s possible to find an incredible home lab server without breaking the bank. However, if you go the route of finding a place in your house or office to put a rack-mount server and/or rack-mount network equipment, it may be difficult depending on your situation.
Once you have your hypervisor of choice up and running on your server and your network is isolated and monitored to your satisfaction, the sky’s the limit for exploration. You can spin up something like Kali Linux or Commando VM, a virtualized firewall like pfSense or OPNsense, various SIEMs, IDS and IPS options, honeypots, vulnerable VMs, containers and apps like Metasploitable 2 or 3, OWASP IoTGoat, OWASP Vulnerable Web Application Directory Applications, Vulnhub VMs, Crackmes.one challenges and other Damn Vulnerable resources. Evaluation versions of Microsoft Operating Systems are also available and can be used to build an Active Directory test environment.
Use these virtual machines and environments to test software and configurations, exploits and mitigations, and various other offensive and defensive techniques. If you have a physical switch and wireless AP in this lab, you can even connect and test physical devices (IoT, Mobile Devices, etc.). The nice part about a home lab is it is private to you and resides within your own controlled internal environment. You get to choose when and what to explore and how you want to explore it. Keep an open mind and think of the possibilities.
Setting up a lab in an isolated cloud environment is also an option but is beyond the scope of this post. Some high-level things to consider when considering cloud labs are the cloud provider costs and the inability to connect physical devices like IoT and mobile devices directly via WiFi, ethernet, etc. However, I encourage you to explore a cloud lab if the topic interests you.
Gadgets, IoT and Hardware
Raspberry Pi
 Raspberry Pi 4
Raspberry Pi 4
With supply chain bottlenecks starting to ease, the pricing and availability of Raspberry Pi devices are beginning to return to pre-pandemic levels. Consider grabbing a Raspberry Pi, or an alternative. These versatile credit card-sized single-board computers can be used for a variety of security-related projects. The relatively low cost of these systems makes them an excellent choice to try out something new with minimal commitment or as part of a home lab. Some examples include:
- Portable Kali Linux System
- Wi-Fi deauth and key capture – Pwnagotchi
- BadUSB – P4wnP1
- DNS Blackholes – Pi Hole or Adguard Home
- Honeypots – HoneyPi or OpenCanary
- Target systems – IoTGoat, RasPwn
 Pwnagotchi/Raspberry Pi 0 W
Pwnagotchi/Raspberry Pi 0 W
In addition to standalone projects like the ones mentioned above, a Raspberry Pi can be used as a multi-tool for hardware hacking through its General Purpose Input Output (GPIO) pin headers. If you have an interest in IoT and hardware hacking, a Pi can provide a low-cost and effective option to reduce the barrier of entry and allow you to tinker.
Finally, there are tons of non-security-focused projects that you can do with a Raspberry Pi which may pique your interest. If you have a spouse or child with an interest in Linux, programming, and/or basic electronics, a Raspberry Pi is a fantastic low-cost option to help encourage their growth and to do something together as a family.
Mobile iOS and Android
Mobile device testing is another topic you may want to build your skills in. Start by reading a few blog posts to get your feet under you. Some apps can be emulated/simulated and tested using free or paid tools including Xcode, Android Studio, Corellium, and Genymotion. Depending on the tool and license chosen, these tools can provide a free or low-cost starting point to test the waters without having to buy physical phones or tablets.
Check out the Damn Vulnerable iOS App and Damn Vulnerable Bank for a couple of training platforms to learn and develop your Android and iOS pentesting skillset. If you find that you want to pursue this topic long-term and on a deeper level, it may be worth picking up a few books or taking a class.
Emulators can only go so far, and if you are planning to pursue this topic, it is ideal if you can pick up a few physical devices. This is especially true if the app that you are testing has special requirements or needs to interact with other physical devices like IoT devices or peripherals. Use your Google skills to find out what other devices people are using and recommend for this purpose. If you happen to have an old device in a drawer somewhere, dig it out and see what you can do with it. If not, eBay and Craigslist are an excellent resource for obtaining used Android and iOS devices. Make sure to do your research to determine the version of Android or iOS running on the device, and if the device can be rooted or jailbroken. Your employer may also have devices for this specific purpose, so it never hurts to ask about training opportunities for their use. If you get a device to use for this purpose, be cautious when you are setting it up. If you connect it to the internet and it auto-updates, you may ruin your chances of rooting or jailbreaking it.
If you have interest or experience in testing the security of iOS itself, check out Apple’s Security Research Device (SRD) and bug bounty program.
Note: Buying pre-rooted and pre-jailbroken devices is not recommended as they could contain malicious software and configurations.
Cloud
Cloud security can be daunting due to the variations from cloud provider to cloud provider, the technologies used, and in the stakeholder’s specific requirements and implementation. In some cloud environments, knowledge of network pentesting is applicable and can help to find the exposure of misconfigured, outdated, and exploitable systems and services. While other environments have a larger focus on web, APIs and cloud-native applications, container orchestration, and identity management.
A good starting place can be in the documentation of the cloud providers themselves with standard reference architectures and diagrams, security reference architecture for AWS, Azure, and Google, and secrets and API documentation.
There are several vulnerable deployment projects to learn and practice with as well, including CloudGoat, Damn Vulnerable Cloud Application, OWASP WrongSecrets, and more. Some of these projects require you to have a cloud provider account and incur the associated costs of spinning up and running cloud resources. Remember that these are intentionally vulnerable cloud deployments so make sure to use them in a non-production and isolated cloud environment and tear them down when you have finished tinkering.
If you have an interest in containers and Kubernetes, make sure to check out InGuardians for training opportunities and Bust-a-Kube to try out an intentionally vulnerable Kubernetes cluster in your local lab VM environment.
Wireless Radio Gadgets
Note: You are responsible for ensuring the wireless activities are legal and in compliance with regulations governing the transmission of radio signals.
Wireless security is more than just Wi-Fi. There are many different wireless tools, standards, protocols, frequencies, radios, and antennas to tinker within this space. Some may be of more interest to you than others and not all of them are useful nor applicable to every situation.
 RTL-SDR
RTL-SDR
If you have an interest in the wireless space in general, a Software Defined Radio (SDR) can be a good place to start, and you can pick up an RTL-SDR for around $50. You can’t transmit with it, but you can receive and begin to learn about tools like GNURadio, gqrx, and Universal Radio Hacker (URH). Amateur Radio books and resources are abundant if you have a passion for the wireless spectrum and want to pursue your Ham license.
To learn about testing traditional 802.11 Wi-Fi networks, I recommend picking up a couple of cheap Panda Wireless adapters compatible with Kali Linux or Rasbian. If you have an old router or access point, you can use it and a laptop, cellphone, or tablet as isolated targets in a test environment. There are lots of free blogs and video resources out there regarding the use of tools like aircrack-ng and kismet. There are also some online training resources that offer virtualized wireless lab networks if obtaining wireless hardware is a limitation for you. PentesterAcademy’s Wi-Fi Security and Pentesting Course is one potential option and is available with a reasonably priced subscription to its training services.
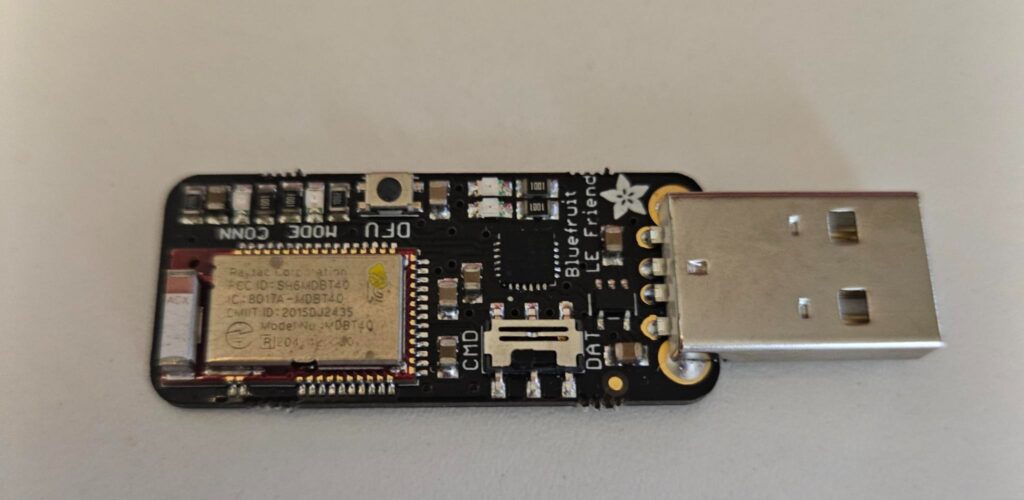 Adafruit BLE Sniffer
Adafruit BLE Sniffer
Bluetooth Low Energy (BLE) is a short-range protocol that is often found in IoT. If you’d like to explore this technology I recommend picking up an Adafruit BLE sniffer and a cheap Bluetooth USB dongle that works with Linux. You can use the sniffer to capture BLE packets in Wireshark and interact with BLE services and characteristics with something like a CSR8510 using tools like hcitool and gatttool. Nordic Semiconductor also has a free mobile app called nRF Connect which is another great option to tinker with BLE by using a cellphone or tablet.
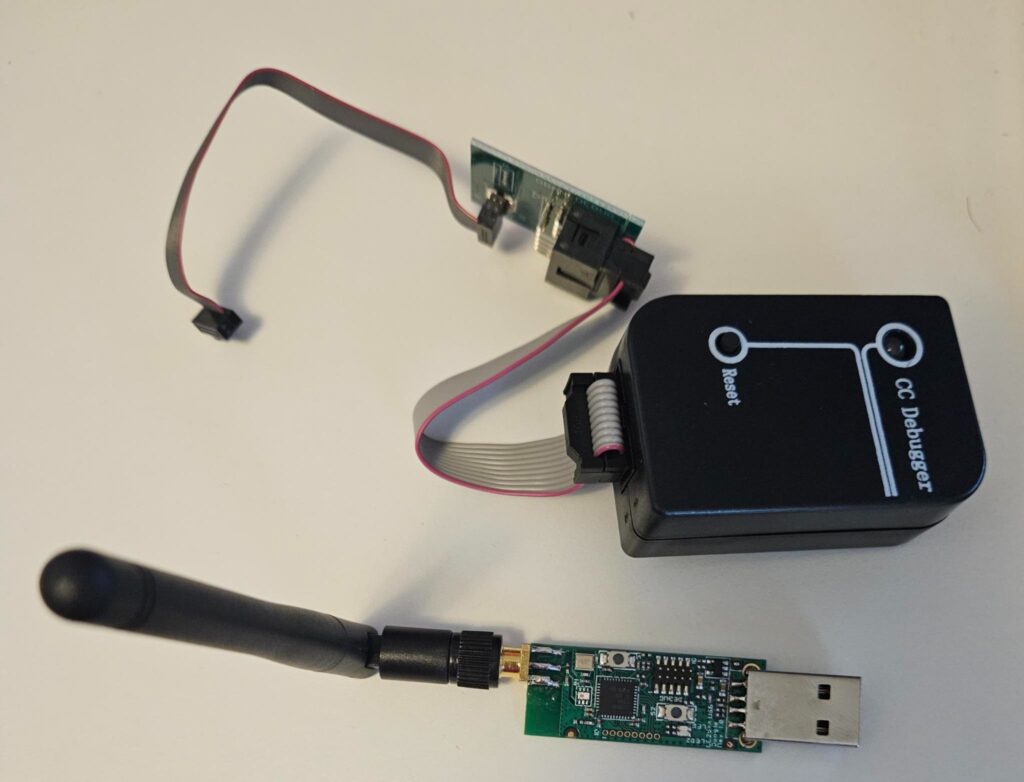 CC2531 (bottom) CC debugger and adapter cable (above)
CC2531 (bottom) CC debugger and adapter cable (above)
Zigbee is another wireless protocol commonly used in the IoT world and can be used to build medium or large mesh networks. If this technology piques your interest, check out the Killerbee framework and the Bumblebee firmware for the TI-CC2531. Note that you will need a programming cable/adapter and a CC debugger to upload the new firmware to the TI-CC2531.
 Flipper Zero
Flipper Zero
A relatively new gadget in the space that has been getting a lot of attention lately is the Flipper Zero. These hacking multi-tools can be used to interact with Sub-GHz radio frequencies, Radio Frequency Identification (RFID), Near Field Communication (NFC), and infrared. Additionally, these devices can be configured to run as Human Interface Device (HID) controllers, BadUSB devices and more. The Flipper Zero also has a GPIO interface which can be used to interact with third-party or home-grown expansion modules further increasing its versatility. It has an extremely active community and considering everything that it can do, a very reasonable price tag under $200.
There are many other RF bands, protocols, and standards that we didn’t cover in this post including Bluetooth, LoRaWAN, Narrowband IoT (NB0IoT), Ultra-wideband (UWB), Z-Wave and more. DigiKey has a couple of articles that can give you a brief primer on some of these and resources to start using in your projects.
Let’s get physical
First, watch the movie Sneakers, next, I would really like to hear you say the word…“passport”. Do you dream of being part of a team whose goal is to perform surveillance, plan, and enter a building by bypassing an RFID door access control and alarm system, all under the cover of darkness? It sounds like something out of a spy movie, but physical security is another skill that you may be interested in developing.
Getting Private Investigator (PI) training and licensure is another option to consider if you have an interest in the physical security space. Surveillance tools and tactics, information-gathering research, and investigation are some of the most important early steps in a successful physical penetration test. Doing some research and developing your skills in social engineering can be extremely important both for information-gathering purposes as well as talking your way into or out of a situation.
 Lockpick (right), tension wrench (center), padlock (left)
Lockpick (right), tension wrench (center), padlock (left)
Although not a skill that is often used during live physical engagements, lock picking is a fun activity that you can practice on your own or with others and can act as a gateway into the physical security space. Buying or making a small set of lock picks, watching a few YouTube videos, or guides, and practicing at home with a few practice locks is all you need to get started.
There are often lock sport and physical bypass security groups that have regular meetups across the country. Lockpicking can be a great way to break the ice and can lead to discussions about books, bypass tools and techniques, common keys, door access control systems, camera and alarm systems, training opportunities, or even access to practice doors and spaces.
Depending on your level of interest in this specialty, it is very easy to collect a lot of (sometimes expensive) tools and gadgets. Unfortunately, practicing your skills with these tools safely, legally, and inexpensively can be even more of a challenge without a safe and appropriate training environment. When you are ready to take your learning to the next level, check out training opportunities from places like Red Team Alliance and The Core Group.
Be aware of your local laws regarding social engineering, impersonation and possession, and intent of lockpicks and “burglary tools”.
Wrapping Up
I hope this post has given you at least one new tool, resource, or project idea to pursue your next educational goal in the infosec space. Small steps like reading a blog or building a pwnagotchi can be a cheap and easy way to test the waters and learn about something new. In some cases, small steps like these can lead to deeper interests, advanced research, and ultimately expertise in an area that you are passionate about. So, embrace your curiosity, go tinker with something, and most importantly, have fun!
