What is it?
In 2014, NIST released the Cybersecurity Framework (CSF) to establish a baseline of security standards intended to identify a core set of baseline measures that any business could measure itself against and implement. The initial developers intended that it “provides guidance to industry, government agencies, and other organizations to reduce cybersecurity risks.”
Several revisions and enhancements have been rolled out, but the fundamental set of 5 “Pillars” upon which the document was created has remained consistent. Each pillar categorizes protections, best practices, or organizational capabilities relevant to the stages of a typical incident response.
The original pillars are:
- Identify (ID)
- Protect (PR)
- Detect (DE)
- Respond (RS)
- Recover (RC)
NIST announced the intent to provide a major revision to the framework back in 2021 to adapt to the changing threat landscape and emerging technologies. On August 8th, 2023, NIST officially pulled back the curtain on CSF 2.0. This major revision is intended to provide better guidance on implementing the framework coupled with some changes in content to reflect the broader scope of technologies, processes, and people under cyber threat.
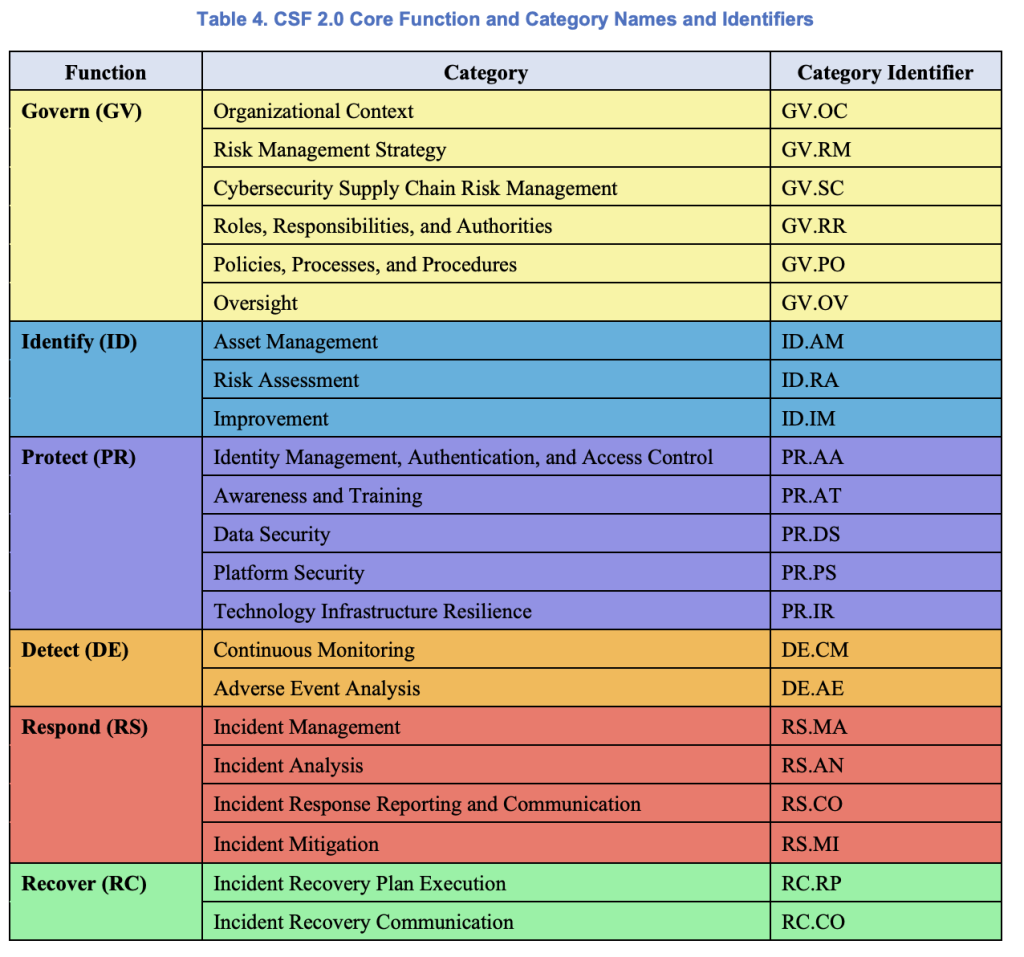
The most apparent change in this version is the addition of a 6th function, Govern (GV). This new function will act as a compendium that binds the 5 existing functions while also being encapsulated by them. It is intended to codify how an organization can prioritize and achieve security functions holistically while aligning with the overall mission, expectations from stakeholders, and compliance requirements.
The figure below, excerpted from the new Framework, is a great representation of how each pillar and function relate to each other and are bound together by the new underlying, Govern function.
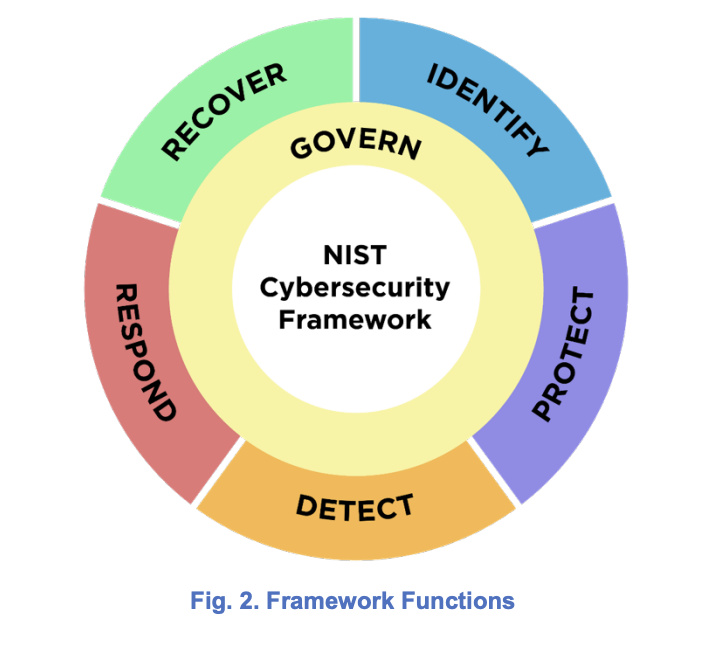
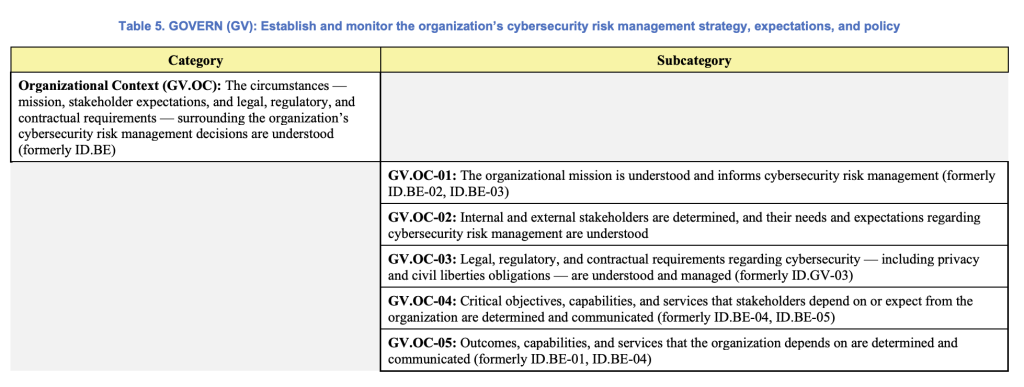
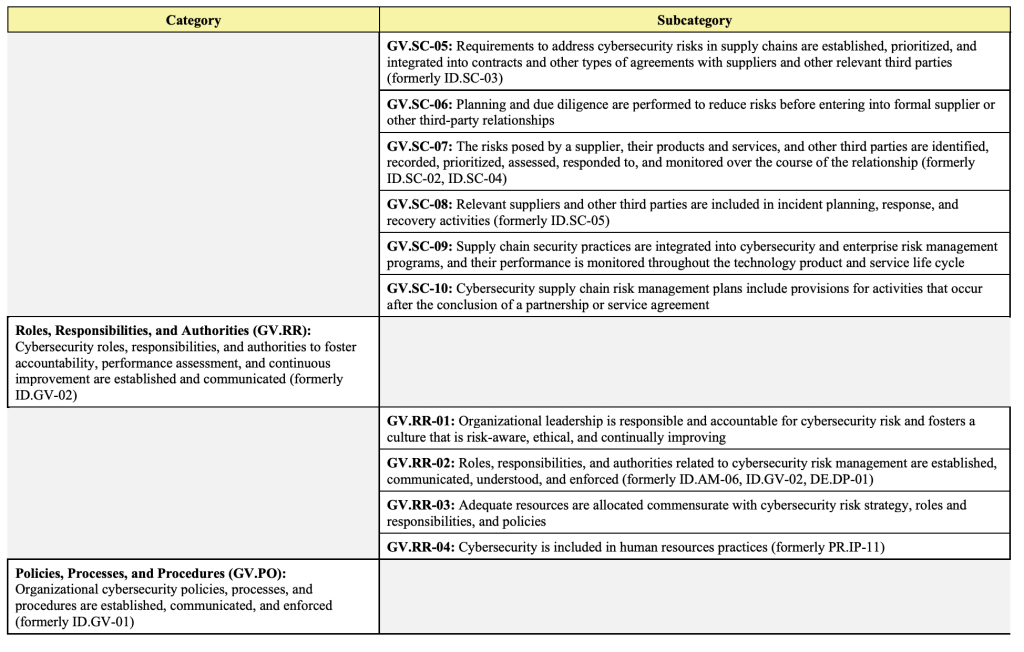
Just like the other functions, Govern contains nested Categories and Subcategories organized to aid in the “operationalizing risk management within an organization.” The proposed Govern function categories include:
- Organizational Context
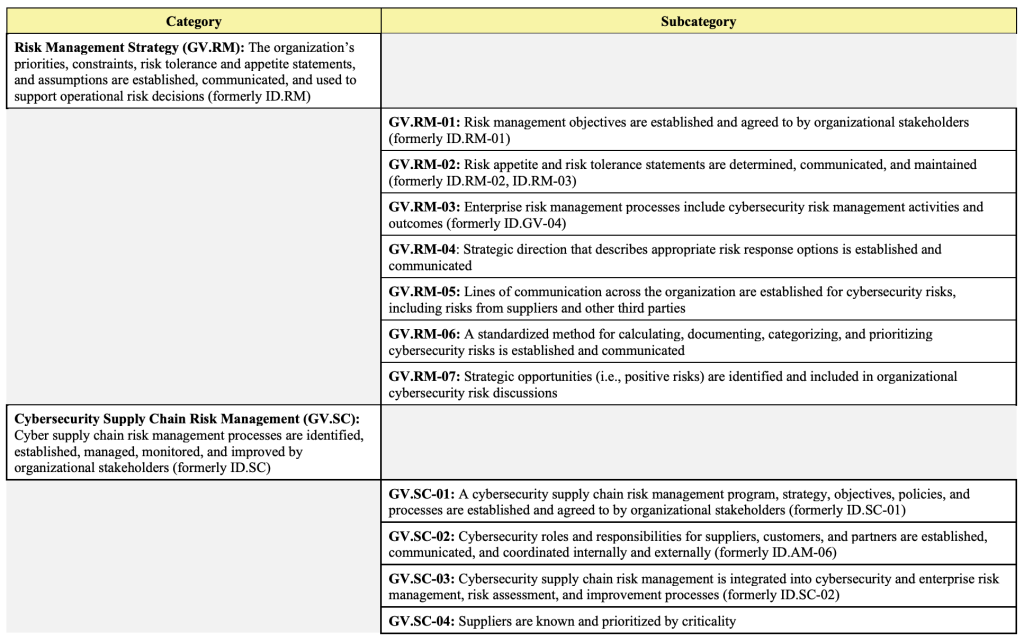
- Risk Management Strategy
- Cybersecurity Supply Chain Risk Management
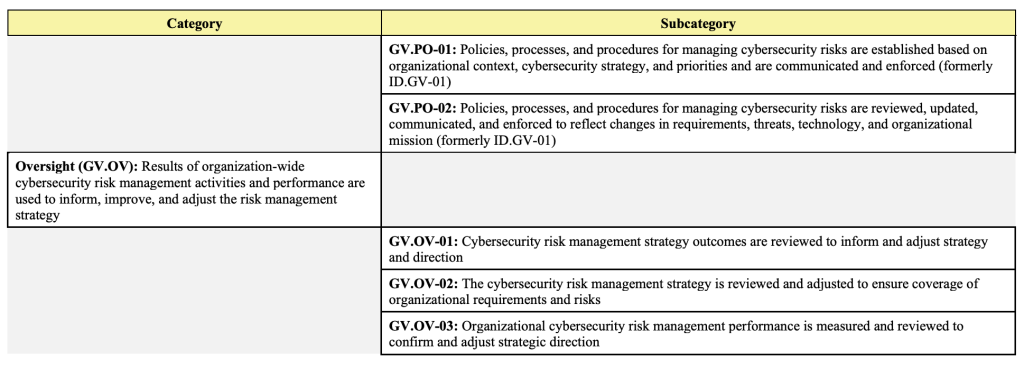
- Roles, Responsibilities, and Authorities
- Policies, Processes, and Procedures
- Oversight
It is immediately apparent to those familiar with older versions of the framework that much of the content has been relocated from the Identify function. This is good news for organizations that have already begun implementing the CSF, as they are likely already adhering to some of the core items in the new function. In fact, the only new category in Govern is the Oversight category, which introduces a formal concept of iteration into the Enterprise-wide Risk Management strategy.
Impacts
Of the added subcategories, NIST’s decision to expand guidance for considerations of the supply chain, especially digital suppliers, highlights the importance of the Cybersecurity Supply Chain Risk Management (C-SCRM) section. As NIST themselves state “The primary objective of C-SCRM is to extend appropriate first-party cybersecurity risk management considerations to third parties”.
While not a new concept, this framework attempts to standardize the security requirements and provide guidance to organizations on the practical application of these controls.
GV.SC-04 states that “Suppliers are (Author’s note: ‘should be’) known and prioritized by criticality”. The explicit inclusion of this standard is a tacit acknowledgment by NIST of the truth that organizations have only a limited picture of some if not most, organizations in their supply chain. This gap has been very publicly demonstrated in recent years through a spate of high-profile supply-chain attacks.
Sharing Relevant Security Testing
While there is no “silver bullet” for any aspect of compliance, the same guidelines that promote a strong operational partnership, namely communication and alignment of interests. What does this look like for Information Security? Some of the more obvious items might include a dedicated communication channel between Security Operations in both organizations, the development of a shared Incident Response Plan, and regular discussions between both Compliance and Information Security.
For more critical supplier relationships, some organizations are beginning to include partners and suppliers in their Penetration Testing, Security Architecture Reviews, and even Tabletop Simulations and Exercises. In these cases, some or all parts of the partner organizations are in-scope, and results are shared with all parties. These engagements yield better results when compared with a traditional assessment or evaluation which is limited to the client’s environment. When presented with a broader scope, one that is representative of the real attack surface, Operators uncover potential supply chain attack paths that would otherwise be impossible to identify before an actual incident.
But how does an organization initiate this understanding and engage partners in this testing? GV.SC-06 provides a potential avenue. It guides that “planning and due diligence are performed to reduce risks before entering into formal supplier or other third-party relationships”. Including this concept of shared Security Testing at the time of entering a partnership may add some complexity to the process, but ensures that the relationship is built on a firm foundation of shared risk and responsibility.
This may require more nuanced tactics when dealing with an already established relationship, but given the additional audit scrutiny on supplier relationships that is implicit in this new CSF pillar, InGuardians firmly believes that organizations should strive to function ahead of the “compliance curve”. Additionally, this approach may allow larger organizations to extend the umbrella of quality security testing to partner organizations that may not have provided sufficient diligence for any number of reasons. It also allows all of the organizations to defer some of the costs associated with a quality Penetration Test, although this comes with a variety of operational and logistical complexities.
In Summary
The NIST CSF’s new version includes explicit consideration for issues of Governance in a way that reflects the complex partner-centric nature of the contemporary business environment.
Organizations already following the key guidance from NIST are already most of the way there, but the formal supply chain risk component highlights an area that most organizations are struggling to get a handle on.
Actively engaging suppliers and partners as a core part of the Information Security function seem the most effective way to address this issue but requires including Information Security interactively as part of the day-to-day operational flow that extends beyond the borders of the organization and well into the supply chain both up and downstream.
NIST’s Framework for the New Govern Pillar
References:
National Institute of Standards and Technology (2023)
The NIST Cybersecurity Framework 2.0. (National Institute of Standards and Technology, Gaithersburg, MD),
NIST Cybersecurity White Paper (CSWP) NIST CSWP 29 ipd.
https://doi.org/10.6028/NIST.CSWP.29.ipd
Written by Brandon Rudolph and Dan Weiss
