InGuardians Labs
Wild West Hackin’ Fest – Kubernetes Attack and Defense: Real Genius Edition
Wild West Hackin' Fest Reno Kubernetes Attack and Defense: Real Genius Edition In this talk, Jay Beale demonstrates Kubernetes and public cloud attacks, attacking a multi-cluster scenario themed on the movie “Real Genius.” We’ll discuss multiple defenses available to...
SolarWinds Supply Chain Attack Leads To Large-scale Exploitation
Last week our industry exploded with a staggering amount of data on the Solarwinds Orion monitoring software which compromised with a backdoor between May and June of 2020. We’d like to provide a little background and some distilled information for our readers. About...
InGuardians Press Release – InGuardians’ Live Online Training launches with top-ranking ‘Assessing and Exploiting Control System and IIoT’ class taught by Justin Searle
FOR IMMEDIATE RELEASE “InGuardians’ Live Online Training launches with top-ranking ‘Assessing and Exploiting Control System and IIoT’ class taught by Justin Searle” Seattle, WA - April 27, 2020 For more than 20 years, InGuardians’ core has been top-tier...
InGuardians Monthly Webinar Series: Most Popular Webinars in 2019
In 2019, InGuardians started a monthly webinar series and hosted one webinar a month. It's been a great experience for our team, and we hope you enjoyed it as well. Here're the most popular webinars in 2019 Hacking And...
The Backup Operators Guide to the Galaxy
Backup Operator accounts are ubiquitous and often overlooked by both blue and red teams. These accounts have abusable permissions and are rarely maintained properly. In this webinar, we will examine and demonstrate novel techniques to stealthily compromise Active...

Software Defined Radio: With Even More Awesome!
On January 31st we started our series of monthly webinars. In our first webinar, Larry Pesce, our Director of Research talks about how to take a radio and turn it into whatever you want with software, for security or fun or both! A brief look at...
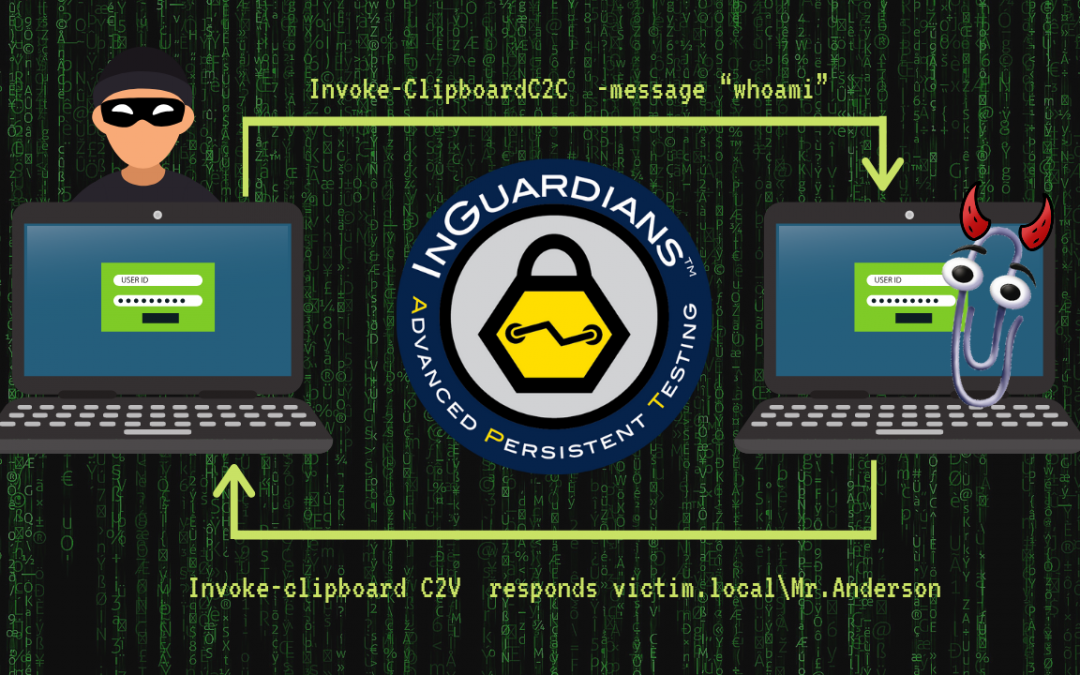
All Your Copy/Paste Are Belong to Us
Author: Adam Crompton, Senior Security Consultant Introduction The clipboard functionality of modern operating systems has been around for decades, implemented to provide the ability to take a bunch of 1’s and 0’s and store them temporarily. In more common...
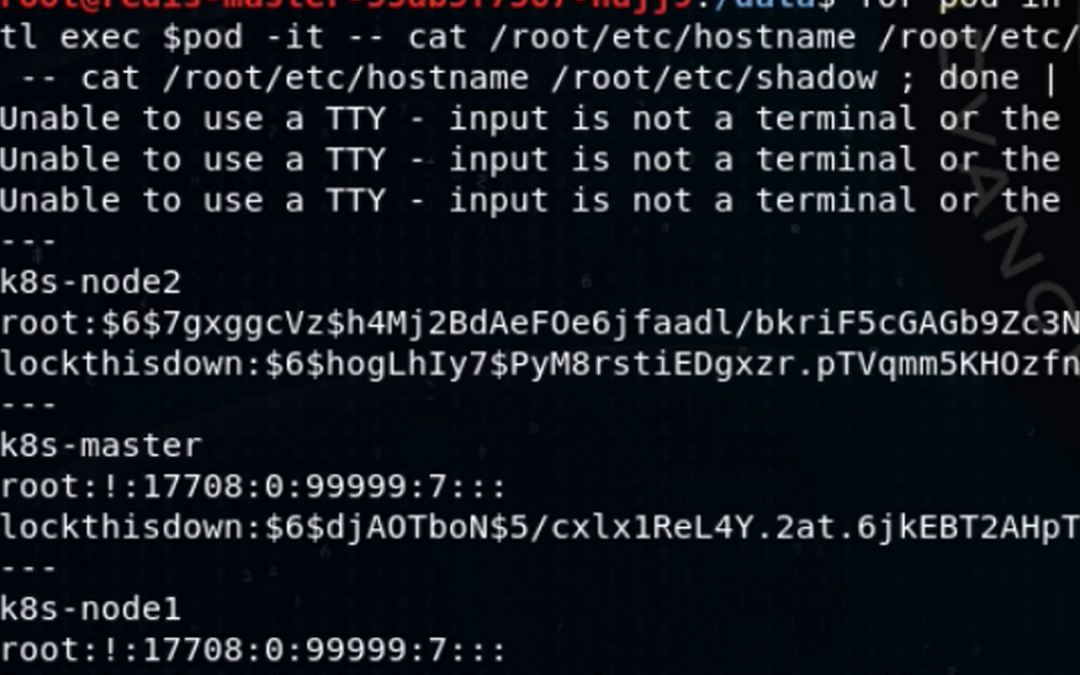
Attacking and Defending Kubernetes: Bust-A-Kube – Episode 1
Jay Beale created two tools used by hundreds of thousands of individuals, companies and governments, Bastille...

12 Things I Learned the Hard Way about being a Project Manager in InfoSec
Over the past eleven and a half years, I have been blessed (or some say cursed) with the opportunity to work in the Information Security industry. When I first stepped in, I had no idea the different levels of client-facing and internal communication struggles I would...
Sparring Board Version 1.2 – Raspberry Pi Edition
Post Author: Don C. WeberTwitter: @cutawayDate Published: 26 July 2013In May 2013 Jay Radcliffe decided that he wanted InGuardians to do something special for Black Hat USA 2013 and DefCon 21 and thus Sparring Board Version 1.2 - Raspberry Pi Edition (SBv1.2) was...
